Removing the Tedium from Your Research Workflow
Linux productivity tools and practices for researchers
SSH login without password
When connecting to a Research Computing cluster via ssh or transferring a file via scp, one needs to enter a password. This page explains how to use SSH keys to handle the authentication step so that logins and file transfers can happen without entering a password.
As indicated in the figure below, the first step is to create private and public “keys” on your local machine (e.g., laptop). These keys are nothing more than files. The public key is then appended to ~/.ssh/authorized_keys on the login node of the desired cluster while the private key remains on your local machine. When you try to connect to that cluster, if the public and private keys match then you will be granted access without needing to provide your password.
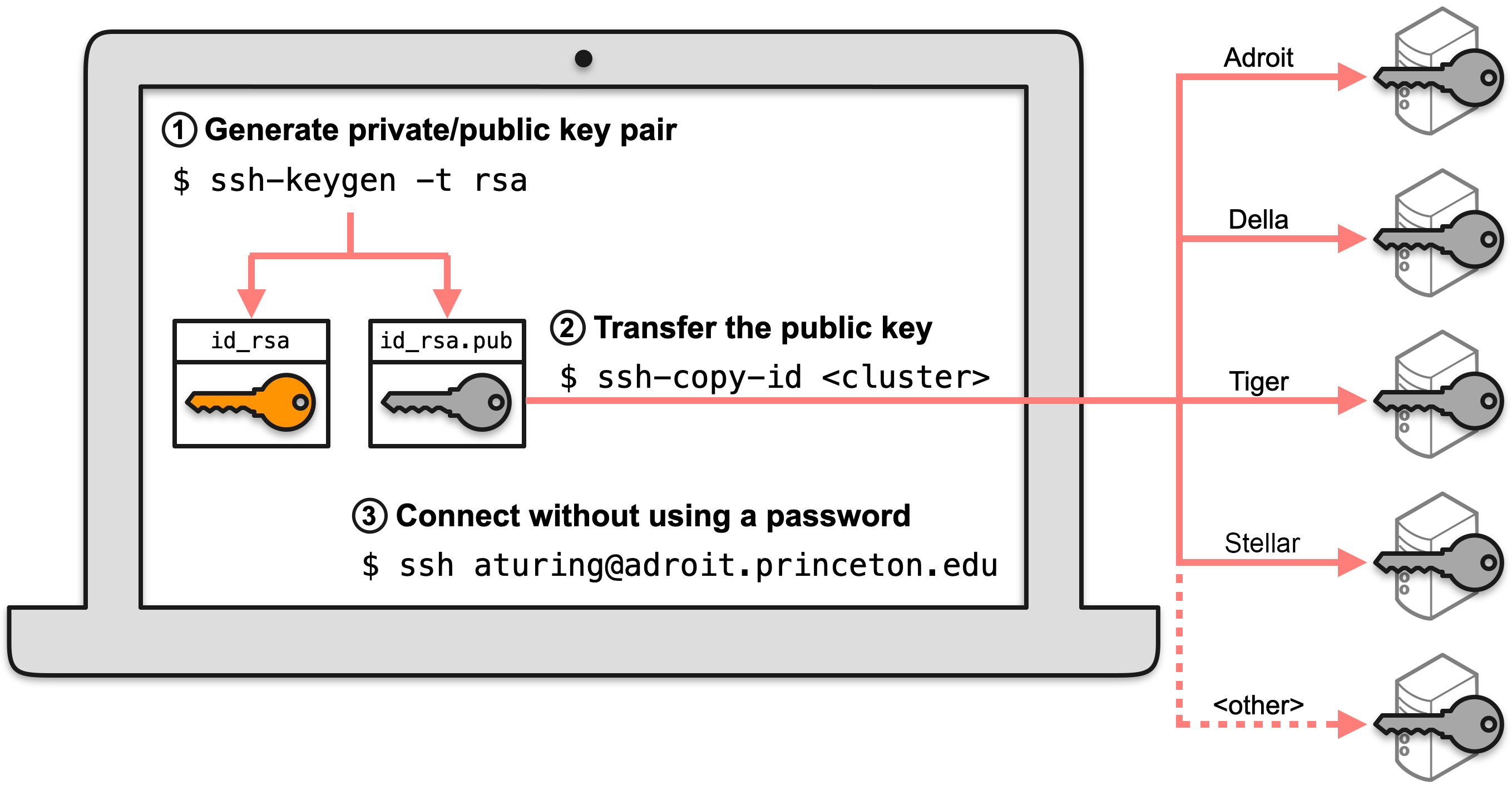
Mac, Linux and WSL
Step 0: See you already have keys
This shows a user that already has SSH keys (id_rsa and id_rsa.pub):
$ ls -l ~/.ssh/
total 72
-rw-r--r-- 1 aturing staff 3965 May 14 10:49 config
drwxr-xr-x 2 aturing staff 64 Apr 17 2024 controlmasters
-rw------- 1 aturing staff 2675 Apr 17 2024 id_rsa
-rw-r--r-- 1 aturing staff 624 Apr 17 2024 id_rsa.pub
-rw------- 1 aturing staff 9293 Sep 2 10:13 known_hosts
-rw------- 1 aturing staff 8711 Jul 21 09:05 known_hosts.old
drwx------ 8 aturing staff 256 Sep 23 14:12 sockets
You may also see keys with names id_ed25519 and id_ed25519.pub.
This user does not have SSH keys:
$ ls -l ~/.ssh/
total 0
Another scenario is the .ssh directory does not exist. In this case, make it:
$ ls -l ~/.ssh/
ls: .ssh: No such file or directory
$ mkdir ~/.ssh
If you do not have SSH keys then continue with Step 1. Otherwise, proceed to Step 2.
Step 1: Create the private/public key pair (if you don’t already have keys)
On your local machine (e.g., laptop), first create the RSA key pair. This is done by running the following command in a terminal (press the “Enter” key 3 times after running the command below, i.e., do not answer any of the questions):
$ ssh-keygen -t rsa
[Enter]
[Enter]
[Enter]
Here is an example:
[aturing@mylaptop ~]$ ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/home/aturing/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/aturing/.ssh/id_rsa.
Your public key has been saved in /home/aturing/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:WAmli4zRUQGWhIHkT4oXi1CjwNJd3KYKNe5OK8DpcZY aturing@mylaptop
The key's randomart image is:
+---[RSA 2048]----+
|+++==*=+. |
|=+o+=..oo. |
|+.o+...oo |
|o.=*...+ |
|+.=++.o S |
|.= E+ |
|..+o . |
| .. o |
| . |
+----[SHA256]-----+
The public key is now located in ~/.ssh/id_rsa.pub. The private key (identification) is located in ~/.ssh/id_rsa. The private key is equivalent to your password so you should never share it. However, you can share your public key and we will do that next.
Step 2: Copy the public key to the Research Computing cluster
Use the ssh-copy-id command to copy the public key to the login node of the desired cluster (enter your password for the Research Computing cluster when prompted):
$ ssh-copy-id <YourNetID>@<cluster-name>.princeton.edu
# answer "yes" when asked "Are you sure you want to continue connecting (yes/no)?"
# enter your password and Duo authenticate (you may not need to Duo authenticate if you established a multiplexed session previously)
Note that the ssh-copy-id command will only transfer your public key. Your private key will remain safe on your local machine in ~/.ssh/id_rsa.
Here is an example session:
[aturing@mylaptop ~]$ ssh-copy-id aturing@adroit.princeton.edu
The authenticity of host 'adroit.princeton.edu (128.112.172.210)' can't be established.
ECDSA key fingerprint is SHA256:Hc3x7Tfs3ULz49U2jmpxzOGNwm2p8mkUnZVs8X1X7g8.
ECDSA key fingerprint is MD5:15:47:21:af:6c:ac:5e:e7:88:d5:de:73:d5:ea:c4:9f.
Are you sure you want to continue connecting (yes/no)? yes
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are ...
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to ...
Password:
Duo two-factor login for aturing
Enter a passcode or select one of the following options:
1. Phone call to XXX-XXX-5201
2. SMS passcodes to XXX-XXX-5201 (next code starts with: 2)
Passcode or option (1-2): 1
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'aturing@adroit.princeton.edu'"
and check to make sure that only the key(s) you wanted were added.
Step 3: Connect to the Research Computing cluster
Try to ssh to the cluster (you should no longer need to enter a password):
$ ssh aturing@adroit.princeton.edu
Or if you worked through Section 1 of this repo then you should be able to use the much shorter:
$ ssh adroit
If you encounter the error Bad owner or permissions on ~/.ssh/config then try doing $ chmod 600 ~/.ssh/config and maybe also $ chown $USER ~/.ssh/config.
Step 4: Return to Step 2 for additional Research Computing clusters
Return to Step 2 and copy the public key using ssh-copy-id to each cluster that you have an account on. Try connecting to that cluster as a test. Remember to do the visualization nodes as well (e.g., adroit-vis, della-vis1, and so on).
Windows
The general recommendation for interfacing a Windows machine with the Research Computing systems is to use Windows Subsystem for Linux (WSL). This would provide a Linux system on your Windows machine. You could then follow the directions above for “Mac, Linux and WSL”. The same is true for SSH multiplexing as discussed in the first section of this repo (i.e., 01_suppressing_duo).
If you decide not to use WSL then proceed through the steps below.
Lanuch a Terminal
This can be accomplished using:
- VS Code
- MobaXterm
- Powershell
- Windows Terminal
Step 0: Checking for SSH Keys
If your username is aturing then look in the following directory for existing keys:
PS C:\Users\aturing> cd .ssh
PS C:\Users\aturing\.ssh> dir
Keys will have filenames like id_rsa and id_rsa.pub or id_ed25519 and id_ed25519.pub. If these files do not exist then you need to make them in Step 1. Otherwise, proceed to Step 2.
Step 1: Create the private/public key pair (if you don’t already have keys)
On your local machine (e.g., laptop), first create the RSA key pair. This is done by running the following command in a terminal (press the “Enter” key 3 times after running the command below, i.e., do not answer any of the questions):
PS C:\Users\aturing\.ssh> ssh-keygen -t rsa
[Enter]
[Enter]
[Enter]
Here is an example:
PS C:\Users\aturing\.ssh> ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (C:\Users\aturing/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in C:\Users\aturing/.ssh/id_rsa
Your public key has been saved in C:\Users\aturing/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:NJas/NpWxce0dsLp5qTDcfAlIJfxvFyIYPE9RojWh2M princeton\jdh4@PVD-SLAB-fabe
The key's randomart image is:
+---[RSA 3072]----+
| ++.=. |
| . o+oE*o. |
| *. =oBBo.|
| . + . +oX+o|
| o S . *o= |
| . . . * |
| .. . B |
| o. + . |
| ... . |
+----[SHA256]-----+
Step 2: Copy the public key to the Research Computing cluster
(Option 1) Try to use ssh-copy-id while replacing aturing with your username:
PS C:\Users\aturing\.ssh> ssh-copy-id aturing@adroit.princeton.edu
If you encounter ssh-copy-id : The term 'ssh-copy-id' is not recognized then use Option 2 below.
(Option 2) If ssh-copy-id is not recognized then run the following command:
PS C:\Users\<username>\.ssh> type C:\Users\<username>\.ssh\id_rsa.pub | ssh <YourNetID>@<HPC-Cluster>.princeton.edu "mkdir -p ~/.ssh && chmod 700 ~/.ssh && cat >> ~/.ssh/authorized_keys"
Below is a specific example for aturing and adroit:
PS C:\Users\aturing\.ssh> type C:\Users\aturing\.ssh\id_rsa.pub | ssh aturing@adroit.princeton.edu "mkdir -p ~/.ssh && chmod 700 ~/.ssh && cat >> ~/.ssh/authorized_keys"
Step 3: Connect to the Research Computing cluster
Try to ssh to the cluster (you should no longer need to enter a password):
PS C:\Users\aturing\.ssh> ssh aturing@adroit.princeton.edu
Or if you worked through Section 1 of this repo then you should be able to use the much shorter:
PS C:\Users\aturing\.ssh> ssh adroit
Step 4: Return to Step 2 for additional Research Computing clusters
Return to Step 2 and copy the public key to each cluster that you have an account on (e.g., adroit-vis, della, stellar, tiger). Try connecting to that cluster as a test.
Looking ahead
Once you have set up passwordless logins, you can run commands on a cluster without formally connecting. For example, the command below will create an empty file with the name myfile in your /home directory on Della:
# on your laptop
$ ssh della "touch myfile"
Note that you can also use the approach above to run scripts on an HPC cluster. For instance, when you start the day, you could run a single command on your laptop that would trigger an analysis script to run.